Email spoofing comes from the word spoof, which is basically another word for falsified. An email has been spoofed when the sender deliberately alters parts of the email to make the message appear as though the email sender, sends emails as someone else. Usually, a spoofed email address will contain personal information such as the sender’s name or email address, and the body of the message is formatted to appear as if they are from a legitimate source.
A spoofed message can appear to be sent from a coworker, a bank, a family member, or any number of seemingly trustworthy sources. A good spoof is quite convincing and will look like any other email that you would normally receive. This is why email phishing remains one of the leading causes of business email compromises along with social engineering attacks.
What are the reasons why people spoof email?
An email is usually spoofed as part of a phishing attack or spear-phishing campaign targeted towards specific employees of an organization.
A spoofed email may also be used to dishonestly market an online service or sell you a product that turns out not to be real. The goal of the email is to trick the recipient into making a damaging statement or releasing sensitive information, such as a password through malicious links. If for example, you’re receiving bounced emails returned to you for messages that you did not send, this could be the result of a spoofing attack on your email service.
How to Identify a spoofed message
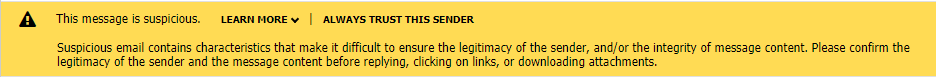
It is imperative that all email users understand that emails that appear to be sent from colleagues or friends can possibly be forged emails. This is the case when scammers will alter different sections of an email to disguise who the actual sender of the message is.
When a user receives an email, they may be able to recognize an email spoofing attempt by hovering over the sender’s email address to see it in fact the expected email address. With some devices or email clients, this level of diligence may not be sufficient to view sender addresses and it will be necessary to open the email headers of a message to view data on email protocols and email authentication via simple mail transfer protocol (SMTP).
Examples of properties with the email that are spoofed:
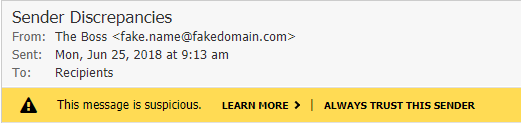
FROM boss@companyexample.com (This will appear to come from a legitimate source on any spoofed message and may make it through spam filters on the receiving server)
REPLY-TO This can also be spoofed, but a lazy scammer will leave the actual REPLY-TO address. If you see a different sending address here, the email may have been spoofed.
RETURN-PATH This can also be spoofed, but a lazy scammer will leave the actual RETURN-PATH address. If you see a different sending address here, the email may have been spoofed.
SOURCE IP address or “X-ORIGIN” address. This is typically more difficult to alter but it is possible to alter the IP of the mail server to another internet service.
These first three properties can be easily altered by using settings in your Microsoft Outlook, Gmail, Hotmail, or other email software. The fourth property above, IP address, can also be altered, but usually requires more sophisticated user knowledge to make a false IP address convincing on a SMTP server (simple mail transfer protocol).

In this example, it appears that the recipient has received a message from their office assistant, requesting money. The subject line should alert you immediately that it is in fact a spam email. This user should contact their assistant through another form of communication to confirm that they did not send this message. Next, you will want to discover who actually sent the message by opening the message headers.
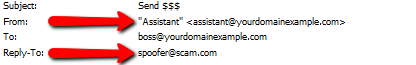
From: field shows the message being sent from “Assistant” assistant@yourdomainexample.com. However, we can also see that the
REPLY-TO: field lists spoofer@scam.com. That is a clear cut example of a spoofed message. You will want to Blocklist any address you find in the
REPLAY RETURN-PATH, and SOURCE IP field that is not an address/IP you normally receive mail from. For more information on viewing and understanding email headers, please see View email headers in Webmail.
How to fight email spoofing
Even with strong email security, the first line of defense against this abuse is user education, If a user receives a spoofed message, please advise them to do the following.
- Blocklist any address/IP listed in the REPLY-TO, RETURN-PATH, or SOURCE IP found within the email headers that you have determined to be fraudulent. See Blacklist addresses, domains, and IPs in Webmail for instructions.
- Immediately change the password of your email account if you or your users provided that information at any point.
- Report phishing emails via our Report Phishing tool.
- Alert other employees within your business of the potential for spear phishing.
- Talk to your email administrator about enabling sender policy framework (SPF record), DKIM and a DMARC policy on your email domain and email server. This will help ensure only people authorized to send email on your domain, are going through to recipients intended on the outgoing email.
Spoofing is possibly the most frustrating abuse issue to deal with, simply put, because domain spoofing cannot be stopped. It doesn’t matter where you host your email, as all email users are potentially vulnerable to spoof attacks, whether you host email with Thexyz, Office 365, Google Workspace etc.
Spoofing is similar to hand-writing many letters and signing someone else’s name to it. This makes tracing or tracking the activity extremely difficult.
If you are an individual and looking to report an abusive email, we recommend reporting email abuse. Our anti-abuse specialists will process the complaint and take the necessary remediation steps. We take email security seriously and are always happy to discuss best practices for avoiding spam.